Human Cyber Risk
Overview
Previously, Security Awareness was primarily treated as a matter of compliance, focusing on ensuring everyone’s attendance at annual trainings for a false sense of security. In addition people should where pointed to hard to read secuirty policies. However, this approach proves ineffective as individuals tend to forget information, and there exist numerous factors beyond knowledge that contribute to their insecure behaviour.

Training & Awareness to Drive Behaviour Change
Our Approach
We recognize that human cyber resilience relies on a combination of Awareness, Behaviour, and Culture (ABC). By integrating these elements, your security measures become people-centric, acknowledging that humans not only act as potential targets but also play a vital role in increasing the difficulty for attackers and thus reducing human cyber risks.
To effectively influence people’s behaviour, security practices need to become seamlessly integrated into their everyday lives, rather than being viewed as an additional burden to their already busy schedules. Training sessions should be concise, allowing individuals to participate at their convenience within their daily routines. Continuous engagement is vital, achieved through subtle prompts and reminders, ensuring that security remains an ongoing aspect of their activities.
Solutions
Human Cyber Risk platform
All over the world, organisations experience cyber-attacks from various bad actors. Often, cyber-attacks result from the actions of humans within an organisation. These actions could generate from the lack of cyber behaviour & culture, negligence, intentional malicious actions, or seeking monetary gains.
The human factor expands until it becomes uncontrollable or hard to manage when a proper cyber awareness plan is absent. In the past, many organisations only relied on security awareness, which they sometimes accompanied with phishing simulations, but it was not effective at all.
As training become repetitive, employees get tired of sitting down for what they admit to being “just another set of training.” Therefore, we recommend micro learning and constant nudges to help encourage teams to develop the right behaviour toward security. By providing technical solutions that aid end-users in identifying specific threats, we can empower them to take control of their own security.

Technology to Help Users and Respond to Threats
Our Approach
Moreover, security teams should offer technical support where appropriate, such as assisting in identifying suspicious emails and providing a centralized repository of answers to common questions. This assistance further empowers individuals to actively contribute to maintaining security without facing overwhelming challenges.
As proactive measures can only mitigate risk to a certain extent, organizations need to devise methods to promptly detect and address specific threats as they arise. Ideally, these responses should be highly automated to minimize the burden on security teams and ensure a swift and efficient reaction.
Solutions
E-Mail Content Analysis
An all-round solution to your email security needs.
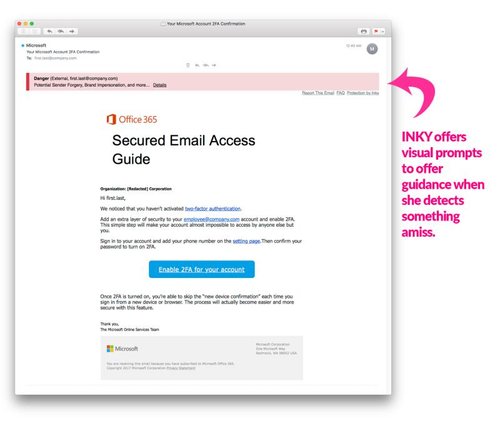
Our service protects your organisation from various email security attacks and helps your team develop positive behavioural change toward adopting healthy cybersecurity practices. It blocks phishing threats, prevents data leaks, and coaches users to make smart inbound, internal, and outbound decisions.
- Inbound Mail Protection: Blocks phishing attempts, and ransomware attacks, coaches users in real time, and makes it easy to report suspicious emails. Shuts down impersonators by detecting unusual behaviour.
- Internal Mail Protection: Say no to account takeovers with sender profiling and social graphing that detects anomalies. Block threats with artificial intelligence that understands behaviour.
- Outbound Mail Protection: Prevents data loss through email errors and malicious insiders. Detects and protects sensitive data.
It analyses and classifies inbound, internal, and outbound emails, helping you stay ahead in cyberspace as impersonation scams, phishing & ransomware attacks increase daily. It detects suspicious behaviour displayed through sophisticated phishing techniques. It makes it easy to report suspicious emails, and the classification from users will enhance further classifications.

Domain Protection
150,000 domains are registered every day. How many will target your business? Anticipate phishing attacks and counterfeiting schemes by monitoring, detecting, and taking-down fraudulent pages before they hurt your brand and business.
Quick, cheap, and lethal. There’s no end to the enduring fame of cybersquatting as a go-to attack vector. In 2020, 20% of cyberattacks started with successful phishing attempts. (Verizon, 2020)
Your team focuses on thousands of doppelgangers at once. This makes domain spoofing a huge strain on your resources, which can lead to alert fatigue and missed true positives.
Focus your efforts on the 0.27% actual threats among ten of thousands of false positives.

